1. Introduction
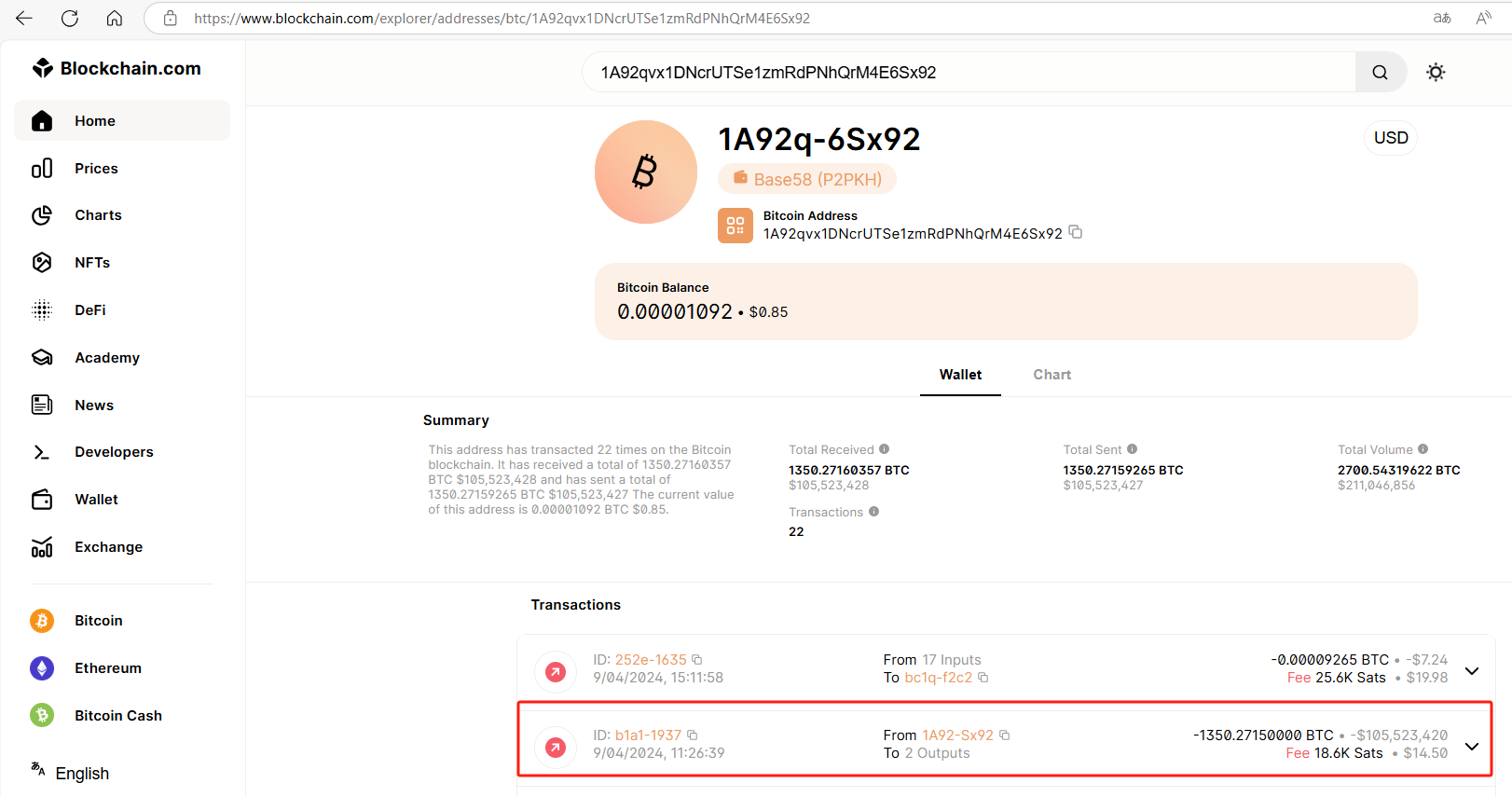
You’re not seeing things: this isn’t clickbait or hype—it really happened. The BTC address was 1A92qvx1DNcrUTSe1zmRdPNhQrM4E6Sx92, and we completed the recovery on September 4, 2024.
I didn’t intend to publicize it so loudly—only a few friends guessed it was me, but I never confirmed it. Now, though, I feel it’s worth celebrating and commemorating this achievement, so I’m writing this account.
The client was a foreigner who, in 2016, bought a Trezor hardware wallet, created a private account, set a strong passphrase, and deposited 1,350 BTC. In 2019, he forgot the passphrase and sought help. Someone once tried brute–forcing it via the Trezor SDK’s PIN interface, but the process was excruciatingly slow. After six months of fruitless attempts, they gave up.
2. Taking the Case
In early July 2024, the client was referred to me and we quickly agreed on a fee. We decided the only viable path was to open the device and read the chip directly. We therefore procured, both in Singapore and domestically, a suite of chip-recovery tools and equipment, and bought ten practice Trezor units.
Although I already knew the theory of chip soldering, practical experience was limited. We spent two intense weeks—day and night—mastering the soldering iron, hot-air rework station, embedded evaluation boards, oscilloscope, chip programmers, flashers, programmable transformers, and more. We practiced on scrap boards until our soldering skills, while not artisanal, were solid enough for the job.
Simultaneously, we drilled ourselves on the actual chip-dump process: designing and soldering bespoke circuits, experimenting with voltages and wiring until we could reliably read the raw flash contents from a Trezor’s secure element.
Once we could extract the encrypted data blob, we needed to decrypt it and recover the passphrase. That took another two weeks of research. We wrote a data-decryption utility, then built and optimized a GPU-accelerated brute-force engine—dramatically improving our throughput.
At the end of July, our intermediary brought us two identical Trezor devices preconfigured with unknown PINs, passphrases, and seed phrases. Relying only on the client’s scant clues, we spent two to three days dumping the chips and, with our GPU-accelerated tool and those hints, successfully recovered the passphrases—giving the client his first glimmer of hope.
By mid-August, the client himself had set up another Trezor with fresh PIN, passphrase, and seed—unknown even to our intermediary—who merely conveyed the same clues. This time, we completed the dump and brute-force in just three to four hours. The client’s faith in our method was fully cemented.
3. The Recovery
In early September, per our agreement, we checked into a hotel with the client and intermediary, signed the contract, and began. Within three hours of receiving the wallet, we had perfectly extracted the chip data. After decryption, we unleashed our GPU rig against the client’s clues.
Twenty-four hours passed with no result despite numerous strategy tweaks. Anxiety grew—if by day 3 we still had no passphrase, the client planned to leave; we would move hotels to continue, but if another two weeks yielded nothing, we agreed to terminate the engagement.
On days 2–3, we and the client reexamined every clue together. Over breakfast on day 3, we distilled the hints further and resumed the run. One or two hours later, still at a standstill, the client went to rest. I suspected some clues were extraneous and overcomplicated. I rewrote a streamlined key-generation module, redeployed it on our GPUs—and within minutes, the passphrase appeared!
We relayed the news to the intermediary, who was overjoyed—he even knelt on the bed in thanks. He then woke the client, who triple-checked and celebrated. After eight years of waiting, it was a triumphant, all-happy ending. The coins were worth 155 × their 2016 cost of USD 375 each—over USD 78 million—so the client had truly attained financial freedom.
Two other domestic friends of the intermediary—a prominent crypto influencer and a well-known lawyer—joined in the celebration.
That night, per contract, we paid out the agreed BTC to client, intermediary, and ourselves; the altcoins were sent later that evening. And just like that, the case closed successfully.
4. Reflections
Looking back, it took us six weeks of tool-building, code-writing, and chip-practice to go from novices to experts in hardware-wallet recovery—a true test of persistence and rapid learning. Ever since, we’ve approached new wallet recoveries with far greater confidence.
The most thrilling moment wasn’t finding the passphrase—it was when the client handed me that Trezor, knowing it held 1,350 BTC. My hands trembled with the weight of that trust.
Despite signing broad disclaimers and achieving repeat successes, I was still fearful of a single misstep wiping out such a fortune. My blood pressure soared—I measured 160/110 mmHg, already Stage 2 hypertension for me—even after my usual meds, I had to calm myself before proceeding. Only after a couple of hours did it normalize enough to continue at ease.
Now, nothing less than a wallet of this magnitude would get my heart racing so much. The crypto world really does harden you—another life-lesson in its own right.
After six weeks of 12–14 hour days, the stress finally caught up: once the job was done, I felt an ache in my coccyx for one to two months, relieved only by copious topical plasters. Success always comes at a price—but this one was worth it.
5. Postscript
I began my PhD in cryptography at Shenzhen University’s ATR National Defense Lab in 2011, dove deep into blockchain in 2013, and started hardware-wallet recoveries in 2019, so I had ample technical and experiential groundwork.
By the end of 2020, we invested over one million RMB in dozens of 8-GPU (RTX 3080/3090) servers dedicated solely to password recovery.
At the close of 2024, we poured 15 million RMB into dozens of 8-GPU RTX 4090 rigs, plus many other systems—to power nothing but wallet-recovery computations. Depending on the wallet type, our cracking speeds now reach billions, hundreds of billions, or even tens of trillions of guesses per second.
I believe no other team in China matches our resolve and infrastructure—because client confidentiality demands that all sensitive data stay on our own servers.
To date, we’ve successfully recovered dozens of wallets valuable in the many-millions. We always honor our commitments: clients receive every satoshi owed, no exceptions.